0%
Every time you book a cab, check your bank balance, or order food online, APIs are quietly doing the heavy lifting. They connect apps, share data, and keep our digital lives running smoothly. But here’s the catch: these invisible engines can also become gateways for attackers. One weak endpoint, one misconfigured permission, and your sensitive data could be exposed in an instant.
That’s why API penetration testing isn’t optional—it’s essential. API pen testing simulates real-world attacks to uncover vulnerabilities in design, implementation, and security controls before hackers can exploit them. From broken authorization to excessive data exposure, it reveals the gaps that truly matter.
Beyond patching security holes, API penetration testing safeguards sensitive data, ensures business continuity, and keeps you compliant with regulations like GDPR and HIPAA. It also shows customers and clients that you take security seriously.
In a world where APIs power nearly every service we rely on, skipping pen testing is like leaving the front door wide open in a busy city—it’s not a question of if someone will strike, but when.
APIs, or Application Programming Interfaces, power the digital world. They let your banking app fetch balances, your ride-hailing app book rides, and your cloud apps sync data seamlessly. But if APIs aren’t secured, they become open doors for attackers. That’s where API penetration testing comes in.
API penetration testing, or API pen testing, is a targeted security assessment that uncovers flaws in API design, implementation, and protection. Instead of waiting for attackers to strike, it simulates real-world attacks to reveal vulnerabilities before they can be exploited.
Why it matters: APIs handle sensitive data and critical services. Key benefits include:
The risks of skipping testing are real. In 2018, Facebook suffered a breach when attackers exploited weak API endpoints, exposing millions of user profiles. The fallout included regulatory fines, lost trust, and long-term reputational damage.
The takeaway is clear: APIs are powerful but fragile. Understanding API security testing helps ensure comprehensive coverage and protects critical endpoints from emerging threats. Penetration testing strengthens them, ensuring they remain secure, resilient, and reliable foundations for growth—without it, they’re among the easiest and costliest targets for cyberattacks.
Before you try to break anything, know what you’re testing and why. API penetration testing is about finding high‑risk gaps fast and fixing them before attackers exploit them. The goal: practical checks that expose real threats, not endless noise.
The key steps for pentesting APIs are:
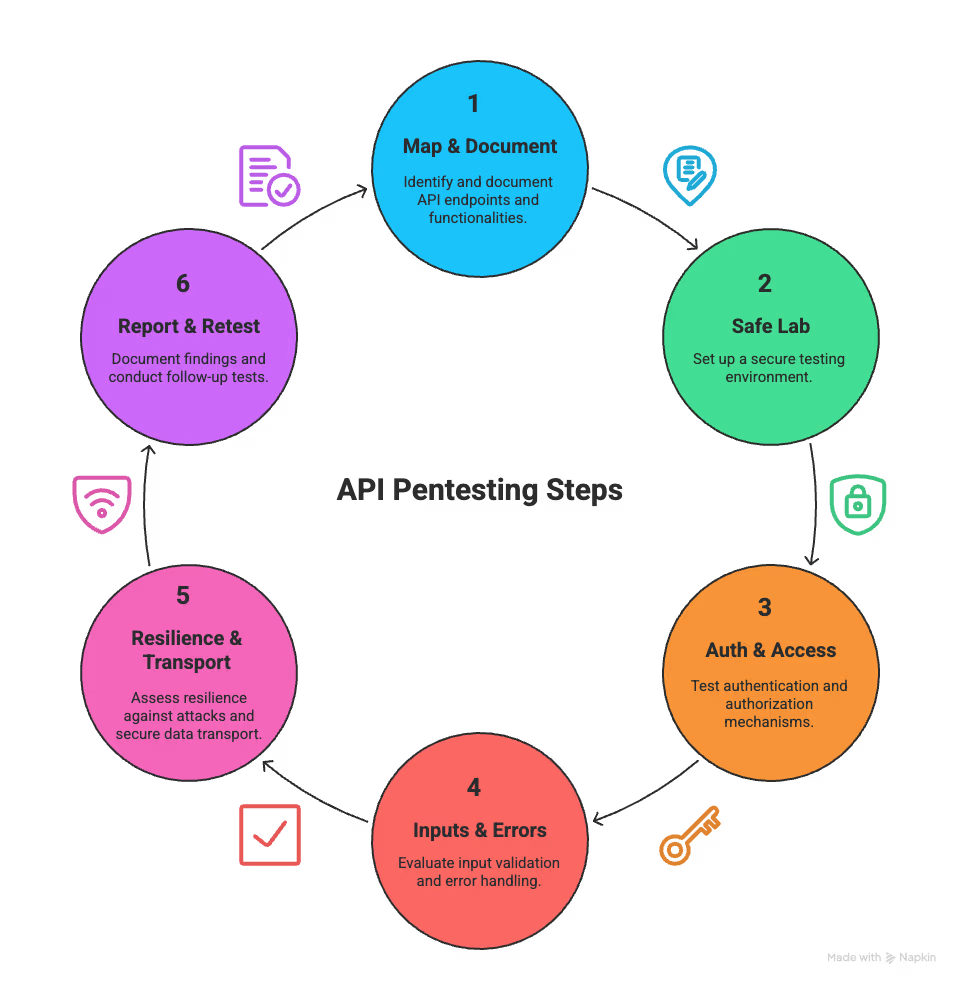
API Pentesting Steps
Each step targets a critical area of API security. Follow them to keep testing structured, efficient, and effective.
Inventory endpoints, HTTP methods, data flows, and client integrations. Pull Swagger/OpenAPI specs, dev notes, and traffic traces. Missing or stale docs are a red flag—they point to forgotten routes, legacy paths, and hidden logic that often contain sensitive fields or weak rules. Start here so every test is focused and efficient.
Stand up an isolated test environment that mirrors production without risking users. Clone staging data, sandbox API keys, and proxy traffic through tools like Postman or Burp Suite. Use realistic payloads, isolate destructive checks, and maintain backups so experiments don’t become outages.
Attack authentication and authorization methodically: test token lifecycle (issuance, expiry, revocation), scopes, session reuse, and role mappings. Attempt horizontal and vertical privilege escalation. Authorization flaws are high‑impact—PoCs should clearly show how access controls fail so teams can patch precisely.
Fuzz parameters, send oversized payloads, and probe encoding edge cases. Watch for crashes, stack traces, SQL errors, or verbose messages that leak internals. Record exact payloads and responses—clear reproduction steps speed remediation and retesting.
Stress endpoints to validate rate limits, throttling, and abuse mitigations. Verify TLS, HSTS, and acceptable cipher suites, and ensure sensitive fields aren’t returned in headers, responses, or logs. Missing throttles or weak transport security enable DoS, interception, and data leakage.
Produce concise, reproducible PoCs with impact, likelihood, and prioritized remediation steps. Include exact requests, observed responses, and practical fixes. After patches, rerun the same PoCs to confirm remediation—verification closes the loop between discovery and secure deployment.
Keep this cycle tight and repeat it regularly. Test, fix, verify: steady rhythm shrinks your attack surface and keeps APIs resilient as they evolve.
APIs power modern apps—but if left unsecured, they’re often the easiest door for attackers. They handle sensitive data, financial transactions, and critical operations, making them high-value targets. Knowing the main risks is essential for 2025.
When APIs don’t properly check if a user can access a resource, attackers can tweak IDs or other parameters to reach data they shouldn’t. Without strict authorization, sensitive user data is at risk. Consistent access checks and testing are essential.
Some APIs return more than necessary—passwords, personal IDs, or payment information. Even seemingly harmless fields can be exploited. Only expose what’s needed for functionality, and always sanitize responses to avoid leaking sensitive info.
APIs without throttling or traffic limits are easy targets. Attackers can flood requests, crash services, or trigger account lockouts and DDoS attacks. Implement strict request limits and continuously monitor for unusual activity.
Endpoints without authentication, outdated libraries, or hard-coded credentials are low-hanging fruit. Attackers exploit these to inject malicious code or access restricted data. Regular endpoint audits, proper authentication, and timely updates are key.
APIs that fail to validate inputs remain vulnerable to SQL, command, or other injection attacks. Malicious inputs can extract data or execute unauthorized commands. Always sanitize inputs and use parameterized queries.
Forgotten test or beta endpoints often remain exposed post-deployment. Attackers actively seek these. Maintain a complete inventory of all API versions and disable anything that isn’t in active use.
Weak TLS, public sensitive endpoints, or misconfigured permissions create easy attack vectors. Regular security reviews, strict access rules, and up-to-date protocols are critical.
APIs are powerful—but fragile. Understanding these vulnerabilities, testing regularly, and fixing gaps proactively ensures your APIs stay secure, reliable, and ready to handle evolving threats.
API penetration testing isn’t one-size-fits-all. Depending on your goals, level of access, and focus, testers can choose different approaches. The three main types are Black Box, White Box, and Gray Box testing.
Black Box Testing treats the API as a complete mystery. Testers focus purely on inputs and outputs, without looking at the underlying code or system internals.
This approach is ideal for functional validation and simulates the perspective of an external attacker. For example, testers might check if endpoints like “Add to Cart” or “Process Payment” behave correctly, without knowing the logic behind them. Black Box Testing highlights vulnerabilities that are visible from the outside.
White Box Testing gives testers full access to the source code, architecture, and internal logic. This allows them to design highly targeted tests to uncover hidden flaws and validate critical security controls.
For instance, a tester could verify authorization checks, inspect discount calculations, or review sensitive algorithms in a shopping cart API. White Box Testing is thorough and efficient, catching vulnerabilities that wouldn’t be visible externally.
Gray Box Testing is a hybrid approach. Testers have partial knowledge of the system—such as architecture, database structure, or API design—but not full source code access.
It combines the benefits of Black and White Box Testing. Testers can identify issues affecting both functionality and internal logic, providing a realistic view of what an attacker with some insider knowledge could exploit. Gray Box Testing is especially useful for layered systems or applications with complex workflows.
Choosing the right testing type depends on your API’s risk profile, available resources, and the depth of insight needed. Often, a combination of these approaches provides the most complete picture of API security.
Securing APIs isn’t just about finding vulnerabilities—it’s about building them out of reach from the start. A few core practices can dramatically reduce your risk and keep attackers at bay.
Implement robust authentication protocols like OAuth 2.0 or OpenID Connect. Make sure authorization checks are enforced consistently at every endpoint. Proper access control ensures users only see what they’re allowed to.
Always use HTTPS to protect data in transit. For highly sensitive information, add extra encryption layers to secure it at rest. Encryption prevents attackers from reading or tampering with your data even if they intercept it.
Never trust incoming data. Sanitize and validate all inputs to prevent injection attacks, buffer overflows, or other malicious payloads. Strong input validation is a simple but effective line of defense against many common vulnerabilities.
Set thresholds on how many requests a user or system can make over time. Rate limiting helps prevent abuse, brute-force attacks, and Distributed Denial of Service (DDoS) attempts, protecting your API and backend systems.
Maintain detailed logs of API interactions. Monitoring allows you to detect anomalies, respond to suspicious behavior quickly, and track potential abuse. Logs are also invaluable during post-incident analysis or audits.
Following these best practices creates a proactive security posture. By enforcing access control, validating inputs, encrypting data, and monitoring usage, you make your APIs much harder to exploit.
Effective API penetration testing starts with the right tools. The right toolkit speeds discovery, exposes real attack paths, and helps teams fix issues faster.
These are the top API Pen testing tools to consider:
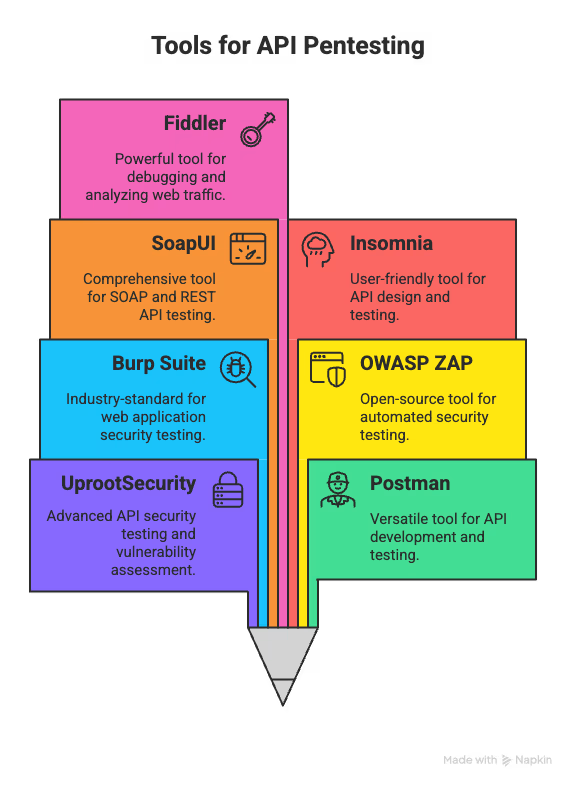
API Pentesting Tools
Let’s get into each tool and what it brings to a practical API pentest.
Uproot Security pairs sharp human-led testing with smart automation to find the subtle, business-critical flaws scanners miss. Expect tailored API pen tests, reproducible PoCs, prioritized fixes, and a pay-per-vulnerability model that focuses effort—and budget—on what actually matters.
Postman is more than a dev client—it offers collections, scripting, and automation. This makes it perfect for rapid endpoint validation, workflow simulation, and repeatable regression or basic security checks.
Burp Suite is the pentester’s go-to toolkit. It allows you to intercept traffic, modify requests, run active scans, and use manual exploitation modules to uncover auth flaws, injections, and logic bugs while producing actionable PoCs.
OWASP ZAP is an open-source scanner focused on automated discovery. It identifies injections, broken auth, and misconfigurations, supports add-ons and CI integration, and is ideal for regular, budget-friendly scans.
SoapUI is designed for SOAP and REST workflows. It simulates message flows, validates schemas, and runs load scenarios, making it great for testing transactional integrity, sequence, and business-critical logic.
Insomnia is a clean, developer-friendly client with scripting, environment management, and response validation. It’s useful for manual testing, chaining requests, debugging auth flows, and reproducing nuanced bugs.
Fiddler is a flexible HTTP/HTTPS proxy for capturing, replaying, and manipulating traffic. It’s excellent for deep debugging, inspecting headers/cookies, and spotting subtle issues automated scanners might miss.
Use Postman or Insomnia for fast validation, Burp or Fiddler for traffic manipulation, and ZAP or SoapUI for automated coverage.These api penetration testing tools together make API pentests thorough, practical, and repeatable.
The API landscape is evolving fast, and staying ahead of threats is critical. As APIs power modern applications, attackers constantly look for gaps, making proactive security strategies essential.
Artificial Intelligence is reshaping API protection. AI tools detect anomalies, flag suspicious activity, and respond to threats in real time. Machine learning analyzes traffic, predicts attacks, and automates mitigation, reducing exposure and helping security teams act faster.
Security is moving left in the development lifecycle. Developers now integrate checks early in design and coding, rather than leaving them for testing or production. This reduces vulnerabilities in live APIs and ensures security is a shared responsibility across teams.
The zero-trust model—“never trust, always verify”—is gaining traction. APIs enforce strict authentication, granular access controls, and continuous verification of users and devices. Even internal systems are treated as untrusted by default, shrinking attack surfaces.
Modern API gateways do more than route traffic. They offer anomaly detection, bot mitigation, rate limiting, and advanced encryption. Gateways act as frontline defenders, blocking attacks while maintaining seamless access for legitimate users.
With AI-driven monitoring, shift-left practices, zero-trust principles, and smarter gateways, API security is becoming more automated, adaptive, and resilient—keeping organizations secure in a rapidly shifting digital world.
Automated tools are fast, but human expertise adds the critical layer of insight. Machines may miss subtle flaws, but our specialists catch them—whether it’s SQL injection, broken authentication, or logic flaws. Uproot Security combines manual and automated testing to ensure every vulnerability is identified and addressed before it becomes a real threat.
Here are the factors that make Uproot Security the ultimate choice for API penetration testing:
With Uproot Security, your APIs stay secure, resilient, and ready to withstand real-world attacks.
API penetration testing isn’t just another security checkbox—it’s an investment in the resilience and trustworthiness of your organization. APIs power critical business functions, handle sensitive data, and connect services across platforms. Each new feature, update, or integration introduces potential vulnerabilities, and attackers are quick to exploit even minor gaps.
Regular API penetration testing ensures that these weaknesses are discovered before they become real-world breaches. It’s not about catching every minor bug; it’s about prioritizing what attackers will exploit first—authentication flaws, exposed data, and weak protections. Combining automated scans with human-led analysis delivers both speed and depth, uncovering subtle issues that tools alone might miss.
Beyond security, penetration testing drives operational confidence. Your teams can deploy updates with assurance, knowing critical endpoints have been stress-tested against realistic attack scenarios. Clients and users also gain trust, seeing that you take proactive measures to safeguard their data.
In a rapidly evolving digital landscape, API penetration testing is more than a safeguard—it’s a strategic investment that protects your data, your reputation, and your business continuity. Regular testing keeps your APIs secure today and ready for tomorrow.

Senior Pentest Consultant