Cybercrime isn’t waiting—and neither should you. The projected global cost? A staggering $23 trillion annually by 2027—up from $8.4 trillion in 2022, according to Anne Neuberger, U.S. Deputy National Security Advisor for Cyber and Emerging Technologies. The takeaway is clear: proactive cybersecurity is no longer optional.
Penetration testing, or pentesting, is a controlled way to see how attackers might breach your systems—conducted with your knowledge and approval. It’s not just about applications. Your entire IT infrastructure—including employees—can be tested. Simulated phishing campaigns, for example, reveal human vulnerabilities before real attackers exploit them.
Automated penetration testing takes this further. It speeds up detection, analysis, and remediation across digital assets, including web applications, APIs, and cloud environments. By shrinking the window attackers have to exploit weaknesses, it strengthens your overall security posture and reduces risk exposure.
This blog dives deep into automated penetration testing—how it works, its benefits and limitations, and where it fits into your security strategy. We’ll also compare it with manual testing, showing how the two complement each other and which approach best suits different organizational needs. By the end, you’ll know when automation is enough—and when the human touch is non-negotiable.
Let’s dive into why automated pentesting is becoming a game-changer for modern security.
What is Automated Penetration Testing?
Automated penetration testing uses specialised software to find security flaws and misconfigurations in applications, APIs, and IT infrastructure. It acts like a real-world attacker, uncovering vulnerabilities and escalating them to their maximum potential impact. From critical business assets to minor endpoints, every area is tested to show how an actual attack could play out.
Many weaknesses stem from open ports, misconfigured setups, or insecure protocols—easy gateways for attackers. Penetration testing exposes these gaps, but it often involves running hundreds or thousands of repetitive test cases across endpoints. Doing this manually is slow, exhausting, and prone to human error. Automation makes it faster, more consistent, and far more efficient.
A common automated technique is fuzzing, where numerous random, invalid, or unexpected inputs are sent to a field to see if it crashes or behaves unpredictably. While fuzzing might only uncover a small fraction of vulnerabilities, automating it saves enormous amounts of time compared to manual checks.
Automated pentesting is widely used for vulnerability scanning, password cracking attempts, and detecting misconfigurations. Web applications are tested for injection attacks—like SQL, LDAP, or mail command injection—broken authentication, and scripting vulnerabilities such as cross-site scripting (XSS). By combining speed, coverage, and real-world simulation, automated penetration testing helps organisations find and fix weaknesses before attackers do.
Automated Penetration Testing vs. Manual Penetration Testing
Manual penetration testing relies on skilled human testers to creatively find and exploit vulnerabilities. Ethical hackers bring flexibility, critical thinking, and contextual awareness that automated tools often miss. They can adapt to evolving threats, understand business logic, communicate findings effectively, and validate results to reduce false positives.
Automated penetration testing relies on specialised software to scan and test systems with minimal human intervention. Humans are typically involved only during setup, troubleshooting, and report verification. Automation excels at speed, efficiency, and continuous coverage, quickly identifying known technical vulnerabilities across large environments. However, it struggles with nuanced issues like business logic flaws, social engineering, or zero-day vulnerabilities.
Here’s a comparison of automated and manual penetration testing:
| Comparison Aspect | Manual Penetration Testing | Automated Penetration Testing |
|---|---|---|
| Cost | Higher due to skilled professionals and longer testing | Lower recurring costs; faster initial execution |
| Speed | Slower, in-depth analysis over days or weeks | Fast, can run continuous scans in minutes or hours |
| Depth & Context | Comprehensive, including logic, social, and complex attack chains | Focuses on known technical vulnerabilities; limited context |
| Flexibility | Adaptable to evolving threats and findings | Limited by preset rules and attack patterns |
| False Positives | Lower due to human validation | Higher due to reliance on signatures |
| Zero-Day Vulnerabilities | Can sometimes identify through creative testing | Typically ineffective |
| Coverage | Targeted, critical focus areas | Broad, standardized coverage across large environments |
| Reporting & Analysis | Detailed, contextual insights for decision-makers | Standardised reports may require human review |
| System Impact | Can modulate intensity to avoid disruption | May stress systems if not properly configured |
Manual testing excels in depth and context, while automation offers speed, efficiency, and broad coverage—making them complementary for a robust security strategy.
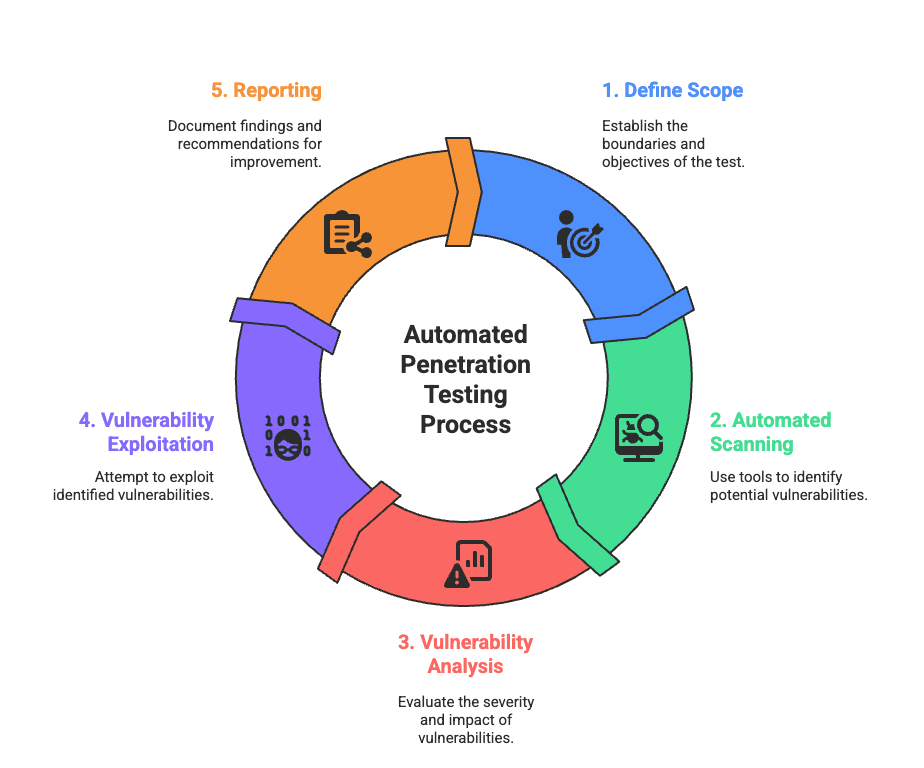
Automated Penetration Testing Process
Automated penetration testing is a systematic approach to uncover vulnerabilities in applications, APIs, and IT infrastructure while simulating the tactics of real-world attackers. Although the exact process may vary across platforms and providers, most follow a set of common stages that ensure a thorough assessment of security weaknesses and their potential impact. Understanding this process helps organisations make informed decisions and strengthen defences proactively.
The standard automated penetration testing process typically includes the following steps:
- Defining Scope
- Automated Scanning
- Vulnerability Analysis
- Vulnerability Exploitation
- Reporting
Let’s go into each step in detail:
1. Defining Scope
The first stage sets the boundaries of the testing environment. It involves identifying the systems, networks, and applications to be evaluated, along with the level of testing required. Defining the scope ensures the automated assessment targets the right areas efficiently while minimizing disruption to business operations. It also helps prioritize critical assets and resources for maximum impact.
2. Automated Scanning
Automated tools, such as vulnerability scanners, network scanners, and web application scanners, systematically examine your systems. These scans detect potential loopholes and weak points that attackers could exploit to access sensitive data or disrupt operations. By covering a wide range of endpoints, automated scanning ensures no critical system is overlooked.
3. Vulnerability Analysis
Once scanning is complete, the gathered data is analyzed against trusted vulnerability databases like ISS X-Force, Symantec/SecurityFocus BID, OSVDB, and NVD (managed by NIST). This analysis identifies threats, prioritizes vulnerabilities, and assesses their potential severity and impact on your business.
4. Vulnerability Exploitation
Detected vulnerabilities are tested to understand their potential impact on applications, operations, and reputation. This step simulates real-world attack scenarios, providing insights into how threats could affect your organization and guiding resource allocation for remediation.
5. Reporting
Finally, automated tools generate comprehensive reports summarizing findings, severity ratings, and actionable recommendations. These reports serve as a roadmap for fixing vulnerabilities and reinforcing overall defenses.
Automated Penetration Testing Process
By following this structured process, organizations gain actionable insights into their security posture. Automated penetration testing accelerates vulnerability detection and complements manual testing, providing continuous protection in a rapidly evolving threat landscape.
Tools Used In Automated Penetration Testing Process
Automated penetration testing relies on specialized tools to execute each step efficiently. Some platforms use a single product suite for multiple stages, while others combine separate tools for more focused tasks. Here’s a detailed look at the key tools used at each stage:
1. Defining Scope
Setting boundaries and identifying targets involves mapping hosts, networks, and services.
-
Nmap – Detects live hosts, open ports, and running services.
-
Metasploit Pro – Defines the testing scope, including target hosts, network ranges, and exclusions.
-
OWASP Amass – Maps external attack surfaces by gathering subdomains, DNS data, and IP addresses.
2. Automated Scanning
Scanning tools reveal vulnerabilities, misconfigurations, and weak points across systems.
-
Nessus – Detects outdated patches, misconfigurations, and network flaws.
-
OpenVAS – Open-source tool for comprehensive network security assessment.
-
Acunetix – Focuses on web applications, spotting SQL injection, XSS, and misconfigurations.
-
Nikto – Checks web servers for outdated software, malicious files, and configuration issues.
-
Qualys Web Application Scanning (WAS) – Cloud-based platform for automated web application security assessment.
3. Vulnerability Analysis. These tools help prioritize risks and assess the potential severity of vulnerabilities.
-
Burp Suite Enterprise – Combines automated scanning with configurable scope.
-
Qualys Vulnerability Management (VMDR) – Analyzes vulnerabilities, prioritizes risks, and integrates remediation workflows.
-
IBM Security QRadar – SIEM tool for centralized threat analysis and correlation.
-
CVE Details & ExploitDB – Online databases to verify known vulnerabilities and exploits.
4. Vulnerability Exploitation
Frameworks simulate attacks to evaluate potential impact and real-world risk.
-
Metasploit Framework – Provides pre-built exploit modules for automated testing.
-
Core Impact – Offers modules for network, web application, and endpoint exploitation.
-
SQLmap – Automates SQL injection attacks to test database security.
-
Commix – Evaluates web application injection vulnerabilities.
5. Reporting
Reporting tools consolidate findings into actionable insights for decision-making.
-
Dradis – Structured platform for collaboration and report generation.
-
Faraday – Automates report creation and integrates findings into workflows.
-
Plextrac – Manages penetration testing reports and tracks workflows.
-
Burp Suite Enterprise Reports – Generates detailed reports for web application vulnerabilities.
Using these tools across each stage ensures automated penetration testing is thorough, efficient, and actionable. They help organizations detect vulnerabilities quickly, prioritize remediation, and strengthen their security posture against evolving threats.
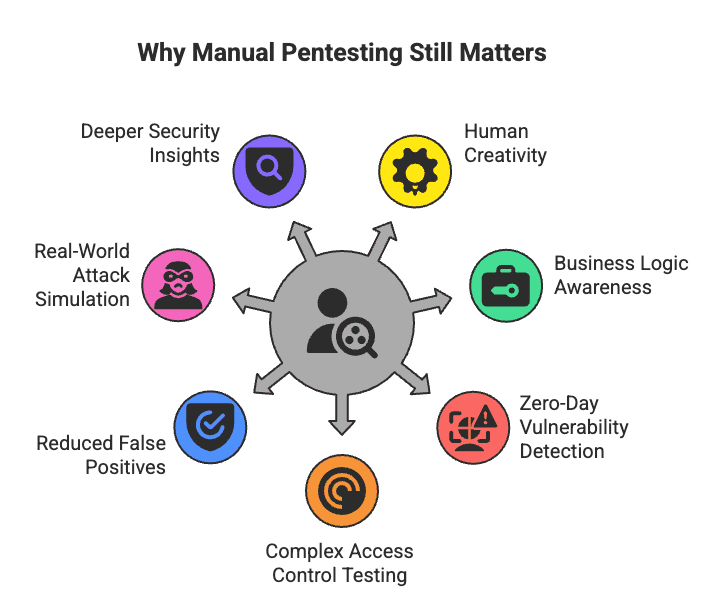
Why Manual Penetration Testing Still Matters
Even with the rapid rise of automation in cybersecurity, manual penetration testing remains a cornerstone of any strong security program. Automation offers speed and scalability, but human-led testing adds a critical layer of depth, adaptability, and accuracy.
Why Manual Pentesting Still Matters
-
Human Creativity and Intuition
AI and automated tools can’t yet replicate the creative problem-solving abilities of the human mind. Skilled testers can adapt mid-test, follow hunches, and pursue unconventional attack vectors that a tool wouldn’t consider—often uncovering issues hidden in plain sight.
-
Business Logic and Context Awareness
Automated scanners excel at detecting known vulnerabilities, but they often miss flaws tied to unique business logic, application workflows, or context-specific behavior. A human tester understands the intended functionality and can identify deviations that create exploitable weaknesses.
-
Detection of Zero-Day Vulnerabilities
Automation relies on existing signatures and vulnerability databases. Manual testers, on the other hand, can hypothesize, test, and discover entirely new vulnerabilities—zero-days—through investigative and exploratory techniques.
-
Complex Access Control Testing
Privilege escalation and intricate access control flaws often require multi-step exploitation that tools struggle to simulate accurately. Manual testers can replicate these scenarios with precision.
-
Reduced False Positives and Negatives
Automated tools can flood reports with false positives or overlook subtle vulnerabilities. Manual testing verifies findings in real time, ensuring only genuine and impactful risks make it to the remediation stage.
-
Real-World Attack Simulation
Humans can integrate tactics like phishing, social engineering, and insider threat scenarios into a test—elements far beyond the capabilities of most scanners.
-
Deeper Security Posture Insights
By blending technical flaw detection with human factor analysis, manual penetration testing provides a holistic, real-world view of your security readiness.
Bottom line: Automation is essential for scale, but manual testing delivers the insight and adaptability needed to stay ahead of attackers. A combined approach ensures maximum security coverage.
How to Choose the Right Penetration Testing Approach?
Choosing a penetration testing approach should never be a “one-size-fits-all” decision. The right choice depends on your organization’s risk profile, infrastructure complexity, regulatory obligations, budget, and testing frequency.
The smartest strategy? Don’t pit manual and automated penetration testing against each other—use them together. Manual testing uncovers complex vulnerabilities that require human insight, while automation delivers speed, scalability, and broader coverage for routine checks. Combined, they ensure both deep, root-level issues and surface-level vulnerabilities are addressed effectively.
To narrow down the right approach for your needs, ask yourself these key questions:
1. What is the nature of my assets?
If you manage highly sensitive systems—such as financial platforms, healthcare records, or critical infrastructure—a manual or hybrid approach is essential. Skilled testers can navigate business logic, context, and advanced attack chains that tools might miss.
2. How often should I conduct testing?
For frequent or continuous checks, automation is your ally. It can run fast, repeatable scans without heavy resource demands. Manual testing is best suited for periodic deep assessments.
3. What is my budget?
Automation is generally more cost-effective for regular scanning. Manual penetration testing, while more expensive, delivers in-depth, targeted evaluations that may save more in the long run by preventing major breaches.
4. What are my compliance needs?
Some regulatory frameworks—like PCI DSS, HIPAA, or SOC 2—require manual penetration testing as part of their audit process. Automated scans alone may not satisfy these mandates.
Bottom line: Use automation for speed and breadth. Use manual testing for precision and depth. Together, they provide the strongest defense against evolving threats.
Power of Blending Automation and Human Skill
Automation is fast. Relentless. Unblinking.
It scans sprawling networks in minutes, flags vulnerabilities, and churns out reports before your coffee cools. It never sleeps, never skips a step, and scales testing across thousands of assets in one go. For routine sweeps and compliance checks, nothing beats it.
But here’s the catch—speed isn’t the same as smarts.
Scanners stick to known vulnerabilities. They can’t improvise, can’t sense patterns out of place, and won’t think, “What happens if I push just a little further?” They miss edge cases, workflow quirks, and the creative exploitation paths only a human tester spots.
That’s where manual testing steps in.
A skilled tester can follow hunches, chain minor flaws into critical exploits, and uncover zero-days automation can’t imagine. They slash false positives and focus on risks that truly matter.
The winning play?
Use both. Automation gives breadth—fast, wide-angle coverage. Manual testing gives depth—context-rich precision.
Because in security, speed without depth is reckless.
And depth without speed is blind.
The blend isn’t optional—it’s the baseline for staying ahead of what’s coming next.
Get security testing that’s fast, accurate, and built for today’s threats. Talk to our team and see how we can keep your systems ahead of attackers.
Frequently Asked Questions

Deep
Senior Content Marketer
