According to 2024 cybersecurity stats from Terranova Security, 98% of web applications are vulnerable to threats. That’s not a minor bug—it’s a systemic risk.
Web applications now sit at the core of modern businesses. They power customer interactions, deliver services, and store sensitive data. But they’re also exposed—and attackers know it.
The rise of AI-assisted development tools like Cursor (the AI code editor) and Vercel’s v0 has made app creation faster and more accessible. Developers can now build and modify apps using simple natural language prompts. But that convenience often comes at the cost of security. These tools are trained on existing codebases, many of which contain the very vulnerabilities that attackers exploit. As a result, insecure code is spreading faster than ever.
That’s why web application penetration testing has become mission-critical. It’s not just about ticking a compliance box—it’s about staying one step ahead of real-world attackers.
In this blog, we break down what web app pentesting involves, how it differs from other testing approaches, and why your business needs it now—not after the next breach. Build smart. Test smarter.
What is Web Application Penetration Testing?
Web application penetration testing is the process of simulating real-world attacks on your web apps—not to break them, but to understand how someone else might. It reveals how attackers could access sensitive data, where your system is vulnerable, and how strong your defenses really are.
These tests can be done externally (like an outsider trying to break in) or internally (as if a trusted insider goes rogue). Either way, the goal is the same: find weaknesses before someone else does.
Unlike automated vulnerability scans, which rely on known signatures and predictable rules, penetration testing adds human creativity into the mix. It uncovers logic flaws, business logic bypasses, and misconfigurations that tools often miss. That’s where manual testing shines—exposing subtle but serious threats.
It’s not just about risk reduction. Web app pentesting also reinforces secure development habits and boosts security awareness across your dev team. In today’s environment, security isn’t a bonus feature—it’s a customer expectation. Failing to meet it can wreck your reputation and business in one breach.
At its core, web application penetration testing serves two critical purposes: to identify exploitable vulnerabilities before attackers do and to provide clear, actionable insights that improve your app’s overall security posture.
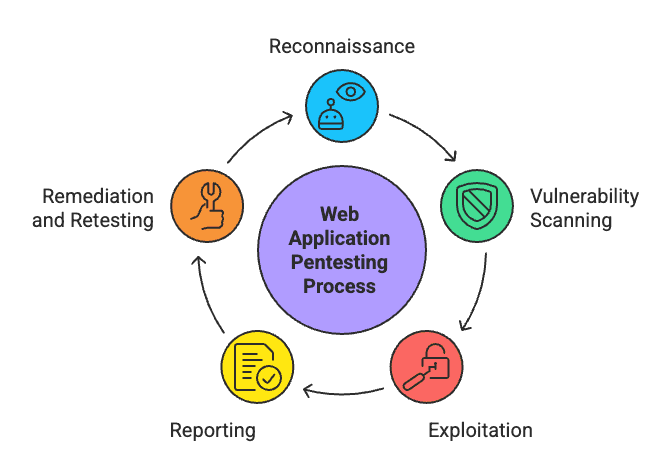
Web Application Pentesting Process
Web application penetration testing isn’t just about hacking into a system—it’s a structured, controlled, and repeatable process designed to identify and fix security weaknesses before an attacker does. A well-executed pentest follows a clear methodology, blending automation with human intuition to uncover vulnerabilities that could be hiding in plain sight.
Here’s how the process typically unfolds:
- Reconnaissance
- Vulnerability Scanning
- Exploitation (Penetration Testing)
- Reporting
- Remediation and Retesting
Let’s get into each of these steps to understand what really happens under the hood.
1. Reconnaissance
This first phase is all about gathering intel before taking any direct action. In white-box tests, organizations often provide internal documentation—like architecture diagrams, API specs, or even login credentials—to speed up discovery. In black-box testing, the tester starts with zero context, mimicking a real-world external attacker.
Recon is further divided into two parts:
-
Active reconnaissance involves directly interacting with the app—browsing pages, submitting forms, inspecting API calls—to map out its structure, input vectors, and authentication flows.
-
Passive reconnaissance gathers intelligence without touching the system, relying on sources like WHOIS records, public repositories, archived pages, subdomain scrapers, and even Google dorking to uncover hidden clues.
2. Vulnerability Scanning
Once the application's surface is mapped, testing moves into discovery. Automated scanners—like Burp Suite, Nikto, or OWASP ZAP—hunt for known vulnerabilities: SQL injection, XSS, broken authentication, outdated packages, and more. Manual techniques catch business logic issues or flaws unique to the app’s architecture that tools often miss.
3. Exploitation (Penetration Testing)
This is where theoretical risks meet reality. Testers exploit the discovered vulnerabilities—carefully and non-destructively—to prove what an actual attacker could achieve. Whether it’s accessing admin panels or dumping user data, this phase helps prioritize remediation based on real-world impact.
4. Reporting
All findings are documented in a structured report. It includes exploited paths, vulnerable components, risk levels, and business impact. Executive summaries highlight key risks, while technical sections support security and dev teams with detailed remediation guidance.
5. Remediation and Retesting
Once fixes are applied, a retest validates that the issues are resolved—not just patched on the surface. This step confirms resilience and closes the loop, ensuring your application emerges stronger and better protected.
Web Application Pentesting Process
Each stage feeds the next. Skipping one breaks the chain—and weakens your defense.
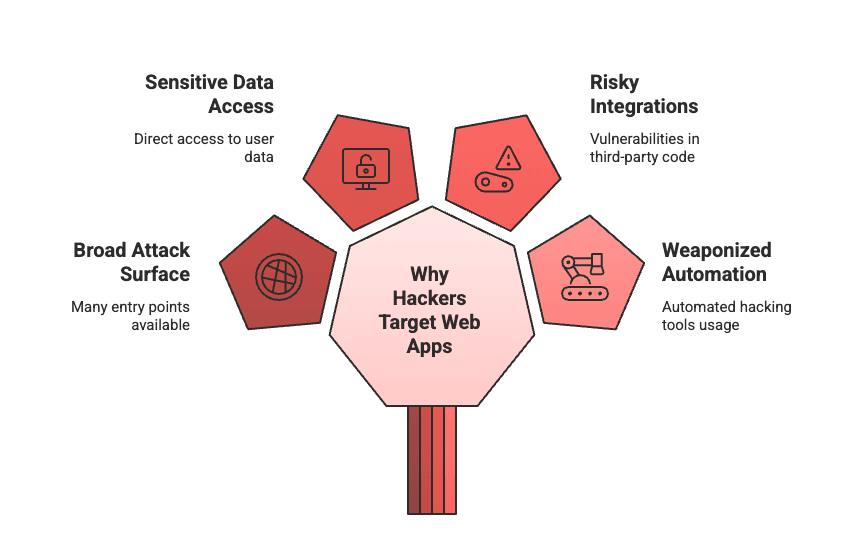
Why Hackers Target Web Apps
Web apps power everything—from digital storefronts to back-office operations. But their visibility, complexity, and connectivity make them irresistible to attackers. Here’s why they top the list of today’s most targeted assets:
The Four Big Reasons:
- A Broad, Growing Attack Surface
- Direct Access to Sensitive Data
- Risky Third-Party Integrations
- Weaponized Automation
Let’s break each one down.
1. A Broad, Growing Attack Surface
Every form field, login portal, and URL parameter in a web app is a potential entry point. With thousands of new apps deployed daily, attackers have a near-infinite pool of targets. Automated scanners and botnets sweep the internet constantly, hunting for weak spots. And all it takes is one overlooked misconfiguration or injection point to let an attacker in—especially when chained with privilege escalation or lateral movement techniques.
2. Direct Access to Sensitive Data
Web apps often handle high-value data—user credentials, payment info, business logic, intellectual property. That makes them a goldmine for hackers. The value of the data isn’t just monetary—it’s reputational, legal, and operational. One breach can lead to identity theft, ransomware attacks, fraud, or regulatory penalties. No wonder attackers go where the data lives.
3. Risky Third-Party Integrations
Modern applications rarely run in isolation. They rely on plugins, APIs, and third-party services to move fast and deliver more. But every external dependency becomes a new risk. One vulnerable open-source component or AI-generated code snippet can act like a trojan horse—bypassing internal defenses and opening a backdoor into your environment.
4. Weaponized Automation
You no longer need elite skills to exploit a web app. Open-source tools like SQLmap and Burp Suite allow even low-skilled attackers to launch complex attacks at scale. Scripts, payloads, and attack chains can be automated and repeated with ease—making attacks faster, cheaper, and increasingly common.
Why Hackers Target Web Apps
In short, web apps present the perfect storm: rich data, wide exposure, and low barriers to attack. Without proactive security measures, they remain one of the easiest—and most damaging—ways into your business.
Manual vs. Automated Web Application Penetration Testing
When it comes to assessing the security of a web application, organizations typically choose between manual and automated penetration testing—or use a mix of both.
Manual testing relies on a skilled human tester’s experience, intuition, and creativity. Though it’s slower and more resource-intensive, it offers deeper insights. Manual pentesters can spot complex, context-driven vulnerabilities—especially those that automated tools often miss.
Automated testing, on the other hand, uses tools to quickly scan for known issues. It’s faster, more scalable, and ideal for regular checks or integration into CI/CD pipelines. But it can generate false positives and often misses logic-based or multi-step vulnerabilities that need human judgement.
Here’s a quick comparison to help you decide what fits your needs:
| Factor | Manual Penetration Testing | Automated Penetration Testing |
|---|---|---|
| Accuracy & False Positives | Fewer false positives; findings are verified by experts. | Higher risk of false positives; manual review still needed. |
| Flexibility & Creativity | Adaptive to unique scenarios and logic flaws. | Limited to predefined test cases and patterns. |
| Time Efficiency | Thorough but time-consuming. | Fast, ideal for frequent checks. |
| Cost | Higher, due to expert time and effort. | Lower, especially for large environments. |
| Coverage | Deep analysis of high-risk areas. | Broad coverage across multiple apps. |
| Contextual Analysis | Understands app logic and user behavior. | Misses logic-driven or contextual flaws. |
| Scalability | Less scalable; resource-heavy. | Highly scalable across environments. |
| Complex Vulnerability Detection | Strong at uncovering chained and advanced threats. | Best for surface-level or known issues. |
Manual testing is ideal for deep-dive assessments and critical apps. Automated testing is better suited for scale and speed. The best security posture often comes from combining both.
When to Choose Manual, Automated, or Both for Web App Pentesting
There’s no one-size-fits-all in web application penetration testing. Manual and automated approaches each bring their strengths—and their blind spots.
Automated testing gives you speed, scale, and repeatability. It’s great for catching known vulnerabilities and integrating into CI/CD pipelines. But it can miss what it doesn’t understand—like complex logic flaws or chained exploits.
Manual testing goes deeper. It brings human intuition into the equation, uncovering subtle, context-driven issues that tools overlook. But it’s slower, more expensive, and not designed for constant repetition.
The smartest approach? Don’t pick sides. Blend both methods based on what your app needs, how often it changes, and what kind of threats you're up against.
Here’s a clear breakdown to help you decide where each method fits best:
| Criteria | Automated Testing | Manual Testing |
|---|---|---|
| Speed & Frequency | Fast, frequent scans; perfect for CI/CD pipelines and continuous testing. | Suited for periodic deep dives, especially after major updates or redesigns. |
| Coverage of Known Vulnerabilities | Quickly detects common and well-documented issues (e.g., OWASP Top 10). | Finds edge-case, custom, or contextual flaws that tools typically miss. |
| Budget & Resources | Cost-effective for regular scanning with minimal human input. | Resource-heavy, but justified when high-risk or regulatory depth is needed. |
| Depth & Complexity | Great for surface-level scans and initial triage. | Uncovers multi-step attacks, business logic flaws, and complex chains. |
| System Complexity | Works best on standardized apps with predictable logic. | Needed for complex, bespoke applications with unique flows. |
| Integration with Dev Process | Seamlessly fits into fast-paced development and DevSecOps cycles. | Best used for validation and real-world threat simulation. |
| False Positive Handling | May report unverified issues — manual review required to confirm actual vulnerabilities. | Only real, exploitable issues are reported — each finding is manually validated. |
Bottom line: Automation gives you breadth. Manual testing gives you depth. You need both to stay secure.
Don’t Let Your Web App Be the Weakest Link
Web applications are the engine rooms of modern business. They’re fast to deploy, cost-effective to scale, and packed with features that customers and teams rely on daily.
But that same accessibility makes them a magnet for attackers.
Most web apps are exposed to the public internet, making them easy to scan, map, and probe.
Even the most robust apps often suffer from overlooked logic bugs, misconfigured permissions, or insecure third-party dependencies—all of which can be exploited with little more than an automated tool and a playbook.
It’s not just about the tech. The stakes are real: leaked customer data, business disruption, legal fallout, and irreversible brand damage.
That’s why web application security isn’t optional—it’s expected. Your customers assume you’re already doing everything you can to prevent breaches. Your partners assume resilience is built-in.
Securing your web app means shrinking the attack surface, patching weak spots, and staying ahead of evolving threats. Whether you’re using manual testing, automation, or a blend of both—make it continuous. Make it real. And don’t wait until after the breach.
Secure your web applications with real-world testing that maps risks, not just vulnerabilities. Talk to our team to get started.
Frequently Asked Questions

Deepraj
Senior Content Marketer
